What is Internet Protocol (IP)?
In order to send somebody information over the internet, you need the correct address – just like sending a regular letter through the mail. In this case however, it is the IP address. Just as a letter receives a stamp to ensure it arrives to the correct recipient, data packets get an IP address. The difference between an IP address and a postal address is that they do not correlate with a specific location per se: instead, they are automatically or manually assigned to networked devices during the connection set up. “Internet Protocol” plays an important role in this process.
- Simple registration
- Premium TLDs at great prices
- 24/7 personal consultant included
- Free privacy protection for eligible domains
The Internet Protocol (IP for short) is the primary protocol in the internet protocol family, and is therefore of fundamental importance when it comes to exchanging messages in computer networks. The connectionless protocol, published in 1974 by the Institute of Electrical and Electronics Engineers (IEEE) and specified as standard in RFC 791, is primarily intended to ensure a successful packet dispatch from sender to addressee. To do this, the Internet Protocol specifies a format that defines what kind of description these data packets have.
Internet Protocol: Definition and history.
Internet Protocol (IP) is a connection free protocol that is an integral part of the Internet protocol suite (a collection of around 500 network protocols) and is responsible for the addressing and fragmentation of data packets in digital networks. Together with the transport layer TCP (Transmission Control Protocol), IP makes up the basis of the internet. To be able to send a packet from sender to addressee, the Internet Protocol creates a packet structure which summarizes the sent information. So, the protocol determines how information about the source and destination of the data is described and separates this information from the informative data in the IP header. This kind of packet format is also known as an IP-Datagram.
In 1974 the Institute of Electrical and Electronics Engineers (IEEE) published a research paper by the American computer scientists Robert Kahn and Vint Cerf, who described a protocol model for a mutual packet network connection based on the internet predecessor ARPANET. In addition to the TCP transmission control protocol, the primary component of this model was the IP protocol which (aside from a special abstraction layer) allowed for communication across different physical networks. After this, more and more research networks were consolidated on the basis of “TCP/IP” protocol combination, which in 1981 was definitively specified as a standard in the RFC 971.
IPv4 and IPv6: What is behind the different version numbers?
Today, those who are concerned with the characteristics of a particular IP address e.g., one that would make computers addressable in a local network, will no doubt encounter the two variants IPv4 and IPv6. However, despite undergoing extensive changes in the past, in no way is this the fourth or sixth generation of IP protocol. IPv4 actually is the first official version of the Internet Protocol, whilst the version number relates to the fact that the fourth version of the TCP protocol is used. IPv6 is the direct successor of IPv4 – the development of IPv5 was suspended prematurely for economic reasons. Even though there have been no further releases since IPv4 and IPv6, the Internet Protocol has been revised since its first mention in 1974 (before this it was just a part of TCP and did not exist independently). The focus was essentially on optimizing connection set-up and addressing. For example, the bit length of host addresses were increased from 16 to 32 bits, therefore extending the address space to approximately four billion possible proxies. The visionary IPv6 has 128-bit address fields and allows for about 340 sextillion (a number with 37 zeroes) different addresses, thus meeting the long term need for Internet addresses.
How is the IP header of a datagram constructed?
As previously mentioned, the Internet Protocol ensures that each data packet is preceded by the important structural features in the header and is assigned to the appropriate transport protocol (usually TCP). The header data area has been fundamentally revised for version 6, which is why it is necessary to specify between the IPv4 and IPv6 headers.
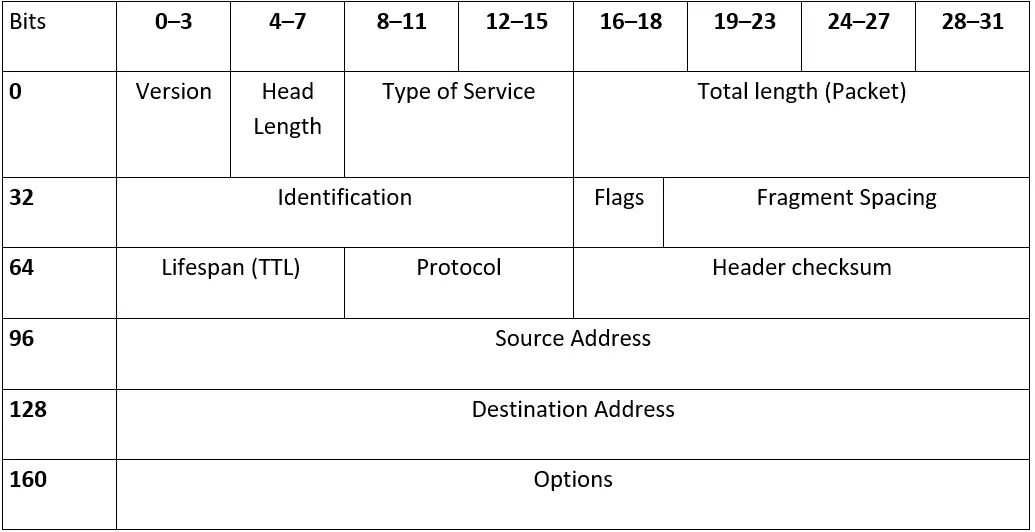
Construction of IPv4 headers
Every IP header always begins with a 4 Bit long specification of the Internet protocol version number – either IPv4 or IPv6. Then there are a further 4 Bits, which contain information about the length of the IP header (IP header length), as this does not always remain constant. The total length of the header is always calculated from this value, multiplied by 32 bits. Thus, the smallest possible header length is 160 bytes (equivalent to 20 bytes) when no options are added. The maximum value is 15 to 480 bit (equivalent to 60 bytes). Bits 8 to 15 (type of service) include instructions for handling and prioritizing the datagram. Here the host can specify the importance of points such as reliability, throughput and delay in data transmission, for example. The total length specifies the total size of the data packet- in other words, it adds the size of the useful data to the header length. Since the field has a length of 16 bits, the maximum limit is 65,635 bytes. It is stipulated in RFC 791 that each host has to be able to process at least 576 bytes. An IP datagram can be fragmented on its way from the host to routers or other devices if desired, but the fragments should not be smaller than the 576 bytes mentioned. The other fields on the IPv4 header have the following meanings:
- Identification: All fragments of a datagram have the same identification number that they receive from the sender. By matching this 16 bit field, the target host can assign individual fragments to a particular datagram.
- Flags: Every IP header contains 3 flag bits, which contain information and guidelines for fragmentation. The first bit is reserved and always has the value 0. The second bit, called “Don’t Fragment”, informs whether or not the packet may be fragmented (0) or not (1). The last “More Fragments“ bit indicates whether further fragments follow (1) or whether the packet is complete or will be completed with the current fragment (0).
- Fragment alignment: This field informs the target host about where a single fragment belongs, so that the entire datagram can be complied again easily. The 13 bit length means that the datagram can be split into 8192 fragments.
- Lifespan (Time to Live, TTL): To ensure that a packet on the network cannot migrate from node to node indefinitely, it is sent with a maximum lifespan (Time to Live). The RFC standard provides the unit of seconds for this 8 bit field, while the maximum lifetime is 255 seconds. The TTL is reduced by at least 1 for each network node that has passed. If the value 0 is reached, the data packet is automatically discarded.
- Protocol: The protocol field (8 bit) assigns the respective transport protocol to the data packet, for example the value 6 for TCP or the value 17 for the UDP protocol. The official list of all possible protocols has been managed and maintained by IANA (Internet Assigned Numbers Authority) since 2002.
- Header/Checksum: The 16 bit “Checksum” field contains the checksum for the header. This has to be recalculated at every network node, due to the dwindling TTL per interim. The accuracy of the user information remains unverified for efficiency reasons.
- Source address and destination address: Every 32 bits (4 bytes) are reserved for the assigned IP address of the originating and target hosts. These IP addresses are usually written in the form of 4 decimal numbers separated by dots. The lowest address is 0.0.0.0., and the highest is 255.255.255.255.
- Options: The options field expands the IP protocol with additional information which is not provided in the standard design. Since these are just optional additions, the field has a variable length, which is limited by the maximum header length. Examples of possible options include: “Security” (indicates how secret a datagram is), “RecordRoute” (indicates all network nodes that have passed, their IP address to follow the packet route), and “Time Stamp” (adds the time at which a particular node was passed).
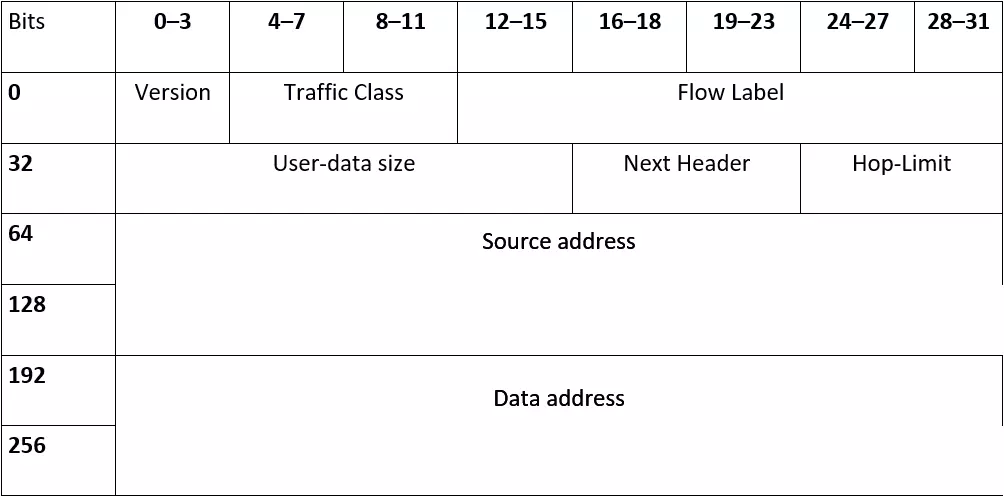
Construction of IPv6 Headers
Unlike its predecessor’s header, the IPv6 protocol has a fixed size of 320 bits (40 bytes). Less frequently required information can be attached separately between the standard header and the user data. These extension headers can be compared to the option field of the IPv4 protocol and can be adapted at any time without having to change the actual header. Amongst other things, you can determine packet routes, specify fragmentation information, or initiate encrypted communication via IPSec. To optimize performance, a header checksum does not exist. Like IPv4, the actual IP header begins with the 4-bit version number of the Internet Protocol. The following field called “Traffic Class” is equivalent to the “Type of Service” entry in the older protocol variant. The same rules apply to these 8 bits as in the previous version: they inform the target host about the qualitative processing of the datagram. A new feature of IPv6 is the FlowLabel (20 bit), which makes it possible to identify data streams from continuous data packets. This allows for the reservation of bandwidth and the optimization of routing. The following list explains the additional header information for the improved IP protocol:
- Size of user data: IPv6 transmits a value for the size of the transported user data, including the extension headers (total 16 bits). In the previous version, this value had to be calculated separately from the total length minus the header line length.
- Next Header: The 8-bit “Next Header” field is the counterpart of the protocol specification in IPv4 and therefore has also assumed its function – the assignment of the desired transport protocol.
- Hop-Limit: The Hop limit (8 bit) defines the maximum number of intermediate stations that a packet can pass through before it is discarded. Just like the TTL in IPv4, the value is reduced by at least 1 with each node.
- Source and destination address: Most of the IPv6 headers contain the addresses of sender and addressee. As previously mentioned, these have a length of 128 bits (quadruple of IPv4 addresses). There are also significant differences in the standard notation. The newer version of the Internet Protocol uses hexadecimal numbers and divides them into 8 blocks of 16 bits each. Double points are used instead of simple dots to separate them. For example, a full IPv6 address looks something like this
2001:0db8:85a3:08d3:1319:8a2e:0370:7344.
How does Internet Protocol addressing work?
In order for the datagrams in their header to make the basic specification of the initial and destination addresses, they must first be assigned to the network subscribers. They are usually assigned between internal and external, or public IP addresses. Three address ranges are reserved for the former, which are used for communication in local networks:
- 10.0.0.0 bis 10.255.255.255
- 172.16.0.0 bis 172.31.255.255
- 192.168.0.0 bis 192.168.255.255
The prefix “fc00::/7” is provided for IPv6 networks. Addresses in these networks are not routed in the internet and can therefore be freely selected and used in private or company networks. Addresses are successfully assigned either by manual input or automatically as soon as the device connects to the network, as long as the automatic address assignment is activated and a DHCP server is in use. With the help of a subnet mask, this type of local network can also be selectively segmented into other areas. External IP addresses are routed automatically by the respective internet provider when they connect to the internet. All devices on the internet via a common router access the same external IP. Typically, the providers assign a new internet address every 24 hours from an address range, which was assigned to them by the IANA. This also applies to the almost inexhaustible arsenal of IPv6 addresses, which are only partly released for normal use. Furthermore, it is not just divided into private and public addresses, but it can be distinguished by much more versatile classification possibilities in so-called “address scopes”:
- Host Scope: The loopback address 0:0:0:0:0:0:0: can use a host to send IPv6 datagrams to itself.
- Link Local Scope: For IPv6 connectivity, is it essential that each host has its own address, even if it is only valid on a local network. This link local address is identified by the prefix ”fe80::/10“ and is used for example, for communication with the standard gateway (router) in order to generate a public IP address.
- Unique Local Scope: This is the aforementioned address range “fc00::/7”, which is exclusively reserved for the configuration of local networks.
- Site Local Scope: The site local scope is an now outdated prefix “fec0::/10”, which was also defined for local networks. However, as soon as different networks were connected or VPN connections were made between networks that were numbered with site-local addresses, the standard was considered overtaken.
- Global Scope: Any host that wants to connect to the internet at least needs its own public address. This is obtained by auto-configuration, either by accessing the SLAAC (stateless address configuration) or DHCPv6 (state-oriented address configuration).
- Multicast Scope: Network nodes, routers, servers and other network services can be grouped into multicast groups using IPv6. Each of these groups has its own address, which allows a single packet to reach all the hosts involved. The prefix “ff00::/8“ indicates that a multicast address follows.
How IP Protocol regulates fragmentation
Whenever a data packet needs to be send via TCP/IP, the overall size is automatically checked. If the size is above the maximum transmission unit of the respective network interface, the information becomes fragmented i.e., deconstructed into smaller data blocks. The sending host (IPv6) or an intermediate router (IPv4) takes over this task. By default, the packet is composed by the recipient, who accesses the fragmentation information stored in the IP header or in the extension header. In exceptional cases, the reassembling can also be taken over by a firewall, as long as it can be configured accordingly.
Since IPv6 generally no longer provides fragmentation and no longer allows router fragmentation, the IP packet must already have a suitable size before sending. If a router reaches IPv6 datagrams that are higher than the maximum transmission unit, the router will discard them and inform the sender of an ICMPv6 type 2 “Packet Too Big” message. The data sending application can now either create smaller, non-fragmented packets, or initiate fragmentation. Subsequently, the appropriate extension header is added to the IP packet, so that the target host can also reassemble the individual fragments after reception.