NTLM (NT LAN Manager)
Computer networks are susceptible to cyberattacks if they are not protected against them properly. Networks are protected by not allowing every single user access to shared data and services. In this way, only a designated user can access a network. Protected entryways have to be integrated into an otherwise closed network. This requires the installation of certain safety procedures. With the NT LAN Manager (NTLM), Windows introduced its own authentication protocol back in 1993, but the protocol is now considered largely outdated. How does ntlm authentication work?
What is NTLM?
NTLM is a collection of authentication protocols created by Microsoft. Initially a proprietary protocol, NTLM later became available for use on systems that did not use Windows. The NT LAN Manager allows various computers and servers to conduct mutual authentication. Most networks attempt to deny access to unauthorized users, which requires implementation of an authentication process.
The protocol requires a client to be authenticated by providing a username and a corresponding password. This allows for an exchange to be established between the user’s device and a server. After the user’s log-in credentials have been recognized, the server can then check access rights and allow the user entry.
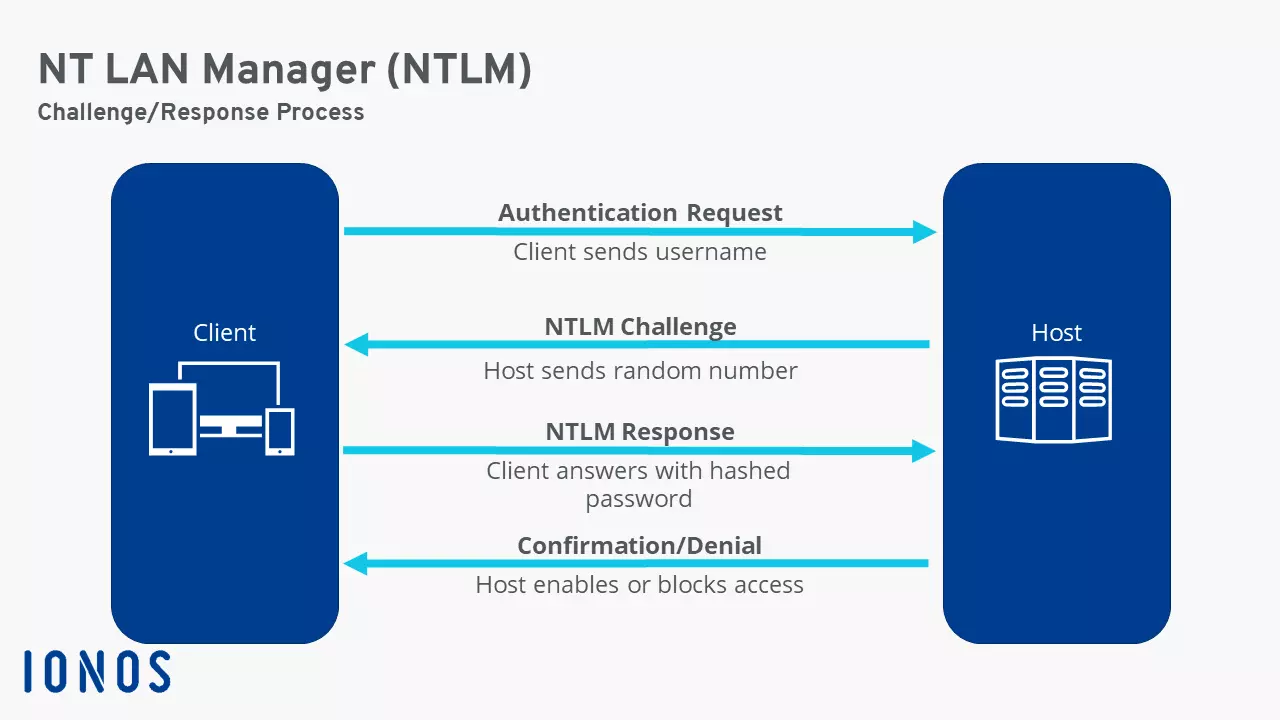
How does NTLM authentication work?
NTLM uses a challenge-response protocol to check a network user’s authenticity. To do so, the client and host go through several steps:
- The client sends a username to the host.
- The host responds with a random number (i.e. the challenge).
- The client then generates a hashed password value from this number and the user’s password, and then sends this back as a response.
- The host knows the user’s password and generates a hashed password value which it can then compare to the client’s response.
- If both values match, the authenticity of the client is confirmed, and network access is granted. If there is no match between the values, the client will be denied access.
To keep a password sent over a network from being read by unauthorized third parties, a hash function is used in which the password is converted into an incomprehensible string of numbers with the help of a mathematical function. Since this conversion cannot be undone very easily, hash functions play a very important role in cryptology.
Information is partially relayed in the form of NTLM flags during the exchange between a client and a host. These are codes with a length of 4 bytes. Negotiation flags, which sometimes only differ from each other by one byte, provide information on the status of the sign-in process.
Applications of NTLM
The NTLM protocol was conceived to connect several Windows machines to one another or to a server. The protocol provides security through the monitoring of clients’ access rights. Windows uses NTLM as a single sign-on process (SSO); users only have to log in once to then have access to various applications within the domain.
NTLM is now considered outdated, and Microsoft uses Kerberos instead. This newer authentication protocol is more secure. However, NTLM is still in use, especially to support older services. If you are an administrator of a larger network, it may be advisable to stop using the NTLM protocol where it is not necessary. This will help to ensure that no client unintentionally logs in to the network while using it, thereby creating a potential security breach.
NTLM protocol: pros and cons of this method
One advantage is that authentication through NTLM does not require users to send passwords unprotected via the network. Password delivery from the client to the server is only done in the form of hashed values which provide a high level of security. However, hashed values have the disadvantage of being equivalent to a password. If the transmission is intercepted, the very security promised by the system can be compromised. Passwords are encrypted through MD4. This process is now considered unsecure since these hashed values can be decrypted with relatively little effort.
A further disadvantage is that NTLM does not include multi-factor authentication (MFA). It is advisable to implement several security mechanisms, especially when sharing sensitive data. The challenge-response protocol in NTLM only allows for a single authentication method: that of using a username and password.